How To Use RemoteIoT Behind Firewall: A Comprehensive Guide
As technology advances, the Internet of Things (IoT) continues to revolutionize the way we interact with devices and systems. However, one common challenge faced by organizations and individuals is managing IoT devices behind a firewall. Understanding how to use RemoteIoT behind a firewall is crucial for maintaining secure and efficient connectivity while protecting sensitive networks.
Whether you're working in a corporate environment or managing personal IoT devices, ensuring secure communication between devices and external networks is paramount. This article will explore the steps and strategies required to effectively use RemoteIoT behind a firewall, ensuring both functionality and security.
By the end of this guide, you'll have a clear understanding of the technical aspects, best practices, and tools needed to overcome firewall restrictions while maintaining robust IoT connectivity. Let's dive in!
Read also:Eit The Revolutionary Technology Explained
Table of Contents
- Introduction to RemoteIoT
- Understanding Firewalls and Their Role
- Overview of RemoteIoT Technology
- Challenges of Using RemoteIoT Behind Firewall
- Solutions to Overcome Firewall Restrictions
- Tools and Software for RemoteIoT Deployment
- Security Best Practices for RemoteIoT
- Designing an Effective Network Architecture
- Implementation Steps for RemoteIoT Behind Firewall
- Troubleshooting Common Issues
- Future Trends in RemoteIoT Technology
Introduction to RemoteIoT
In the realm of IoT, RemoteIoT represents a cutting-edge solution for managing and monitoring devices remotely. This technology enables seamless communication between IoT devices and centralized systems, even when they are located behind firewalls. The ability to control and access devices from afar is particularly valuable in industries such as manufacturing, healthcare, and smart home solutions.
RemoteIoT leverages advanced networking protocols and encryption techniques to ensure secure data transmission. By integrating with existing infrastructure, it simplifies the process of managing large-scale IoT deployments while maintaining network security.
This section provides a foundational understanding of RemoteIoT and its significance in modern IoT ecosystems.
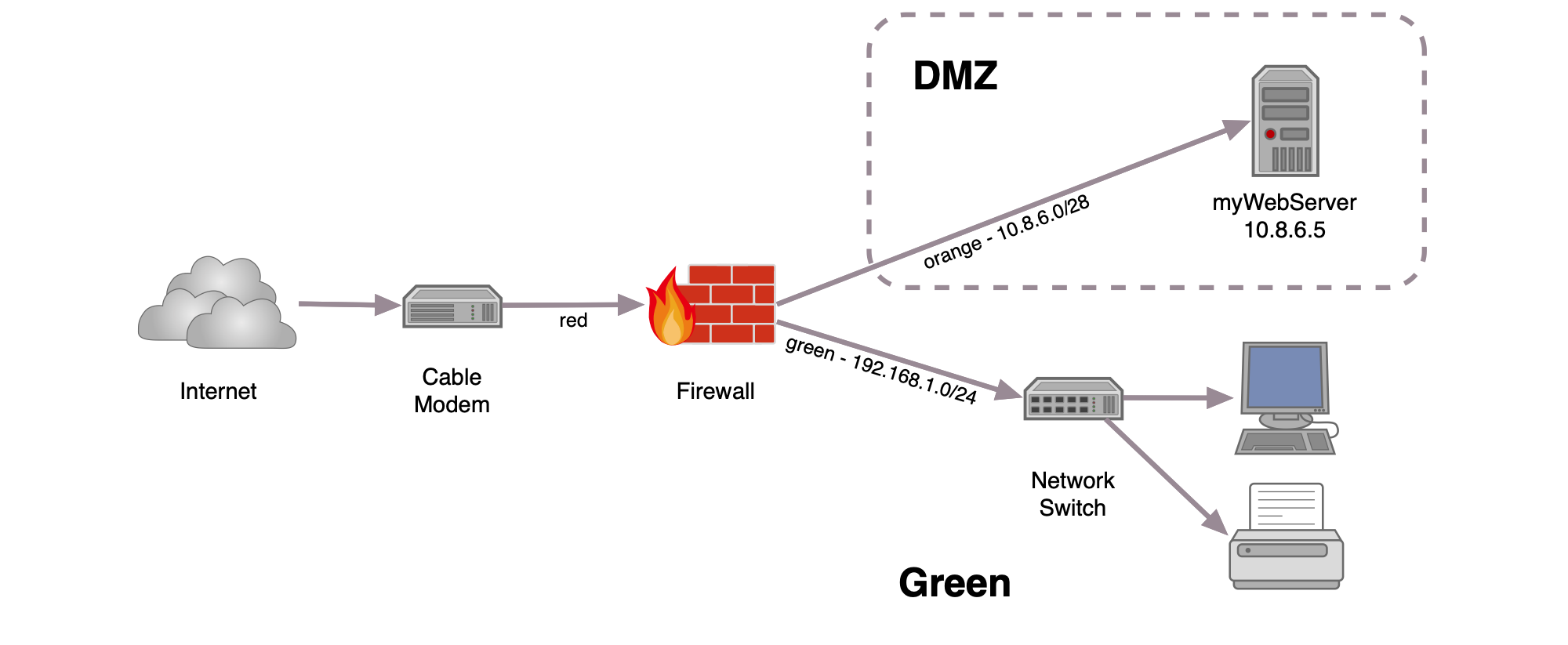
Understanding Firewalls and Their Role
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its primary function is to act as a barrier between trusted internal networks and untrusted external networks, such as the internet. Firewalls play a critical role in protecting sensitive data and preventing unauthorized access to networks.
Types of Firewalls
There are several types of firewalls, each designed to address specific security needs:
- Packet Filtering Firewalls: Examine packets at the network layer and allow or deny them based on predefined rules.
- Stateful Inspection Firewalls: Track active connections and evaluate packets in the context of the connection state.
- Application-Level Gateways: Operate at the application layer and provide advanced filtering capabilities.
Understanding the role of firewalls is essential when deploying RemoteIoT solutions, as they can impact device connectivity and data transmission.
Read also:Carlos Villagran The Iconic Life Of A Beloved Comedian
Overview of RemoteIoT Technology
RemoteIoT technology enables users to access and manage IoT devices remotely, regardless of their physical location. It utilizes a combination of cloud-based platforms, APIs, and secure communication protocols to facilitate seamless interaction between devices and centralized systems.
Key features of RemoteIoT include:
- Secure data encryption
- Real-time monitoring and control
- Scalability for large-scale deployments
- Integration with existing IoT ecosystems
By leveraging these features, organizations can enhance operational efficiency and improve device management capabilities.
Challenges of Using RemoteIoT Behind Firewall
Deploying RemoteIoT behind a firewall presents several challenges, primarily related to security and connectivity. Firewalls are designed to block unauthorized access, which can interfere with the communication between IoT devices and external systems. Below are some common challenges:
- Network Restrictions: Firewalls often block certain ports and protocols, limiting device connectivity.
- Latency Issues: Encrypted connections may introduce delays, affecting real-time data transmission.
- Security Concerns: Ensuring data privacy and protection against cyber threats is paramount.
Addressing these challenges requires a strategic approach that balances security with functionality.
Solutions to Overcome Firewall Restrictions
To effectively use RemoteIoT behind a firewall, it's essential to implement solutions that address the challenges outlined above. Below are some practical strategies:
1. Port Forwarding
Port forwarding allows specific ports to be opened on a firewall, enabling communication between IoT devices and external systems. This method requires careful configuration to ensure only necessary ports are exposed.
2. Virtual Private Networks (VPNs)
VPNs create encrypted tunnels between devices and networks, ensuring secure communication even behind firewalls. They are widely used in enterprise environments for remote access.
3. Cloud-Based Gateways
Cloud-based gateways act as intermediaries between IoT devices and external systems, bypassing firewall restrictions while maintaining security.
By implementing these solutions, organizations can overcome firewall limitations and ensure uninterrupted RemoteIoT connectivity.
Tools and Software for RemoteIoT Deployment
Several tools and software solutions are available to facilitate RemoteIoT deployment behind firewalls. These tools provide features such as device management, data encryption, and network monitoring. Some popular options include:
- MQTT Broker: A lightweight messaging protocol ideal for IoT applications.
- OpenVPN: A robust VPN solution for secure remote access.
- Node-RED: A visual programming tool for IoT device integration.
Selecting the right tools depends on specific use cases and requirements, ensuring optimal performance and security.
Security Best Practices for RemoteIoT
Security is a top priority when deploying RemoteIoT behind firewalls. Implementing best practices can significantly reduce the risk of cyberattacks and data breaches. Below are some key recommendations:
- Use Strong Authentication: Implement multi-factor authentication (MFA) for device access.
- Encrypt Data Transmission: Utilize secure protocols such as TLS/SSL for data encryption.
- Regularly Update Firmware: Keep IoT devices and software up to date with the latest security patches.
By adhering to these practices, organizations can enhance the security of their RemoteIoT deployments.
Designing an Effective Network Architecture
A well-designed network architecture is crucial for successful RemoteIoT deployment. It involves planning and configuring network components to ensure optimal performance and security. Key considerations include:
- Segmentation: Divide the network into smaller segments to isolate IoT devices and reduce attack surfaces.
- Load Balancing: Distribute network traffic evenly to prevent bottlenecks and improve performance.
- Monitoring and Logging: Implement monitoring tools to detect and respond to security threats in real time.
By designing a robust network architecture, organizations can maximize the potential of RemoteIoT while maintaining security.
Implementation Steps for RemoteIoT Behind Firewall
Implementing RemoteIoT behind a firewall involves a systematic approach to ensure successful deployment. Below are the key steps:
Step 1: Assess Network Requirements
Evaluate the network infrastructure and identify potential challenges, such as firewall restrictions and bandwidth limitations.
Step 2: Configure Firewall Settings
Adjust firewall rules to allow necessary ports and protocols for RemoteIoT communication.
Step 3: Deploy Security Measures
Implement encryption, authentication, and monitoring tools to safeguard the network.
Following these steps ensures a smooth and secure RemoteIoT deployment process.
Troubleshooting Common Issues
Despite careful planning, issues may arise during RemoteIoT deployment. Below are some common problems and their solutions:
- Connection Failures: Verify firewall rules and ensure required ports are open.
- Data Latency: Optimize network configurations and use efficient communication protocols.
- Security Alerts: Investigate and resolve any security incidents promptly.
By addressing these issues proactively, organizations can maintain reliable RemoteIoT operations.
Future Trends in RemoteIoT Technology
The future of RemoteIoT technology looks promising, with advancements in artificial intelligence, edge computing, and 5G networks driving innovation. Key trends to watch include:
- AI-Powered Analytics: Enhancing data processing capabilities for better decision-making.
- Edge Computing: Reducing latency by processing data closer to the source.
- 5G Connectivity: Enabling faster and more reliable communication for IoT devices.
Staying informed about these trends will help organizations leverage the full potential of RemoteIoT in the years to come.
Kesimpulan
Using RemoteIoT behind a firewall requires a strategic approach that balances security with functionality. By understanding the challenges, implementing effective solutions, and adhering to best practices, organizations can successfully deploy and manage IoT devices in secure network environments.
We encourage readers to share their thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT technology and its applications. Together, let's shape the future of connected devices!