Securely Connect Remote IoT VPC Raspberry Pi: Free Download And Comprehensive Guide
In today's interconnected world, securely connecting remote IoT devices to a Virtual Private Cloud (VPC) using a Raspberry Pi has become increasingly essential for both hobbyists and professionals. With the rise of smart devices and remote work, ensuring secure communication between IoT devices is paramount. This article delves into the step-by-step process of setting up a secure connection, including free download options and practical tips to safeguard your IoT network.
Whether you're a beginner or an experienced tech enthusiast, understanding how to configure a secure IoT environment is crucial. From selecting the right tools to implementing best practices, this guide will provide you with actionable insights to protect your devices and data.
As we explore the topic of securely connecting remote IoT VPC Raspberry Pi, we will also discuss free download resources that can simplify the process. By the end of this article, you'll have a comprehensive understanding of the tools, techniques, and strategies to keep your IoT infrastructure secure.
Read also:Cimena Saenz The Rising Star In The Entertainment Industry
Understanding IoT Security and Its Importance
What is IoT Security?
IoT security refers to the technologies and practices used to protect IoT devices and the networks they connect to. These devices, ranging from smart thermostats to industrial sensors, often lack robust security measures, making them vulnerable to cyberattacks. Securely connecting remote IoT devices ensures that sensitive data remains protected and unauthorized access is minimized.
Why is IoT Security Crucial?
IoT devices are increasingly integrated into critical systems, from healthcare to manufacturing. A breach in one device can compromise an entire network, leading to data theft, financial loss, or even physical harm. By securing remote IoT VPC connections, you can:
- Protect sensitive information from unauthorized access.
- Prevent malicious actors from taking control of your devices.
- Ensure compliance with industry regulations and standards.
Common IoT Security Threats
Understanding potential threats is the first step in securing your IoT environment. Some common threats include:
- Device hijacking: Attackers gain control of IoT devices to perform malicious activities.
- Data breaches: Unauthorized access to sensitive data transmitted between devices.
- Firmware vulnerabilities: Exploiting outdated or unpatched firmware to infiltrate devices.
Setting Up a Virtual Private Cloud (VPC) for IoT Devices
What is a VPC?
A Virtual Private Cloud (VPC) is a secure and isolated network environment provided by cloud service providers. It allows you to host and manage your IoT devices within a private network, ensuring that communication between devices remains secure and protected from external threats.
Benefits of Using a VPC for IoT
Implementing a VPC for your IoT devices offers several advantages:
- Enhanced security through network isolation.
- Flexible configuration options for device management.
- Scalability to accommodate growing IoT deployments.
Steps to Create a VPC for IoT Devices
Setting up a VPC involves the following steps:
Read also:Unlocking The Power Of Remoteiot Vpc Your Ultimate Guide
- Select a cloud provider that supports VPC creation, such as AWS, Azure, or Google Cloud.
- Define your network parameters, including IP ranges and subnets.
- Configure security groups and access control lists (ACLs) to restrict unauthorized access.
- Deploy your IoT devices within the VPC and test connectivity.
Using Raspberry Pi for Secure IoT Connections
Why Use Raspberry Pi for IoT?
Raspberry Pi is a versatile, low-cost device that serves as an excellent platform for IoT projects. Its compatibility with various operating systems and programming languages makes it ideal for setting up secure connections between IoT devices and a VPC.
Setting Up Raspberry Pi for IoT
Here's how you can configure a Raspberry Pi for secure IoT connections:
- Install an operating system such as Raspbian or Ubuntu on your Raspberry Pi.
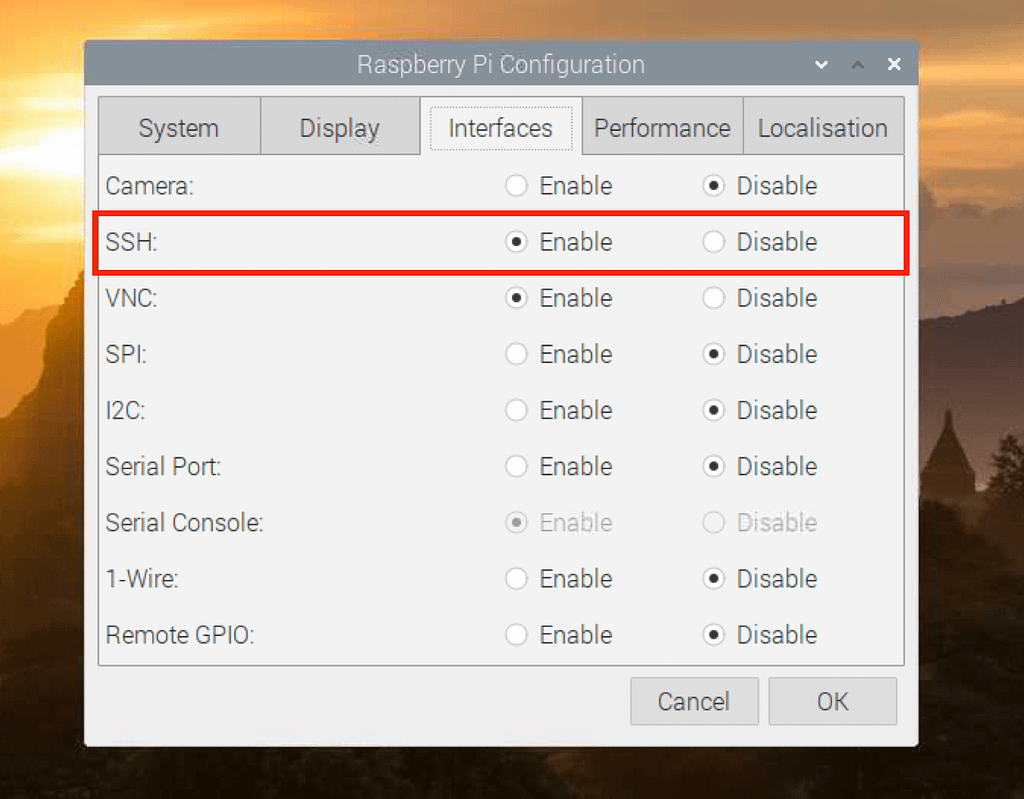
- Configure SSH (Secure Shell) for remote access and ensure it is secured with strong authentication methods.
- Install necessary software packages, such as MQTT brokers or SSL/TLS libraries, to facilitate secure communication.
- Test the connection between your Raspberry Pi and IoT devices to ensure proper functionality.
Securing Raspberry Pi for IoT Deployments
To ensure the security of your Raspberry Pi in an IoT environment, consider the following best practices:
- Change default passwords and use strong, unique credentials.
- Regularly update the operating system and installed software to patch vulnerabilities.
- Implement firewalls and intrusion detection systems to monitor and block suspicious activities.
Free Download Resources for Secure IoT Connections
Where to Find Free Tools
Several free tools and resources are available to help you securely connect remote IoT devices to a VPC using a Raspberry Pi. Some popular options include:
- MQTT Brokers: Mosquitto and HiveMQ offer free versions for small-scale deployments.
- Encryption Libraries: OpenSSL and GnuTLS provide robust encryption capabilities.
- Network Monitoring Tools: Wireshark and Nmap can help identify and mitigate potential security threats.
How to Choose the Right Tool
When selecting free tools for your IoT project, consider the following factors:
- Compatibility with your Raspberry Pi and IoT devices.
- Ease of installation and configuration.
- Community support and available documentation.
Best Practices for Using Free Tools
To maximize the effectiveness of free tools in securing your IoT environment:
- Regularly update tools to ensure they have the latest security patches.
- Document your configurations and settings for future reference.
- Test tools in a controlled environment before deploying them in a production setting.
Implementing Secure Communication Protocols
Overview of Communication Protocols
Secure communication protocols are essential for protecting data transmitted between IoT devices and a VPC. Common protocols include:
- MQTT (Message Queuing Telemetry Transport): Lightweight and ideal for resource-constrained devices.
- CoAP (Constrained Application Protocol): Designed for low-power and low-bandwidth networks.
- HTTPS: Provides secure web communication using SSL/TLS encryption.
Configuring MQTT for Secure IoT Connections
To configure MQTT for secure communication:
- Install an MQTT broker on your Raspberry Pi or a cloud-based server.
- Enable SSL/TLS encryption to secure data transmission.
- Set up username and password authentication for authorized access.
Ensuring Data Integrity
Data integrity is critical in IoT environments. To ensure data remains unaltered during transmission:
- Use digital signatures to verify the authenticity of data.
- Implement checksums to detect and correct errors.
- Regularly audit logs to identify and address any discrepancies.
Best Practices for Securing IoT VPC Connections
Network Segmentation
Segmenting your network ensures that IoT devices are isolated from other systems, reducing the risk of lateral movement in case of a breach. Use VLANs or subnets to create distinct network zones for your IoT devices.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and ensures compliance with security standards. Automate audits using tools like Nessus or OpenVAS to streamline the process.
Employee Training and Awareness
Human error is a significant factor in security breaches. Educate your team about IoT security best practices and encourage them to report any suspicious activities promptly.
Future Trends in IoT Security
Emerging Technologies
Several emerging technologies are shaping the future of IoT security:
- Blockchain: Provides decentralized and tamper-proof data storage.
- AI and Machine Learning: Enhances threat detection and response capabilities.
- Quantum Cryptography: Offers unparalleled encryption strength for secure communications.
Regulatory Landscape
As IoT adoption grows, governments and organizations are developing regulations to ensure data privacy and security. Staying informed about these regulations is crucial for maintaining compliance.
Adapting to New Challenges
The evolving threat landscape requires continuous adaptation. Stay updated with the latest security trends and invest in tools and training to address emerging challenges.
Conclusion
Securing remote IoT VPC connections using a Raspberry Pi involves a combination of technical expertise, strategic planning, and adherence to best practices. By following the steps outlined in this guide, you can protect your IoT infrastructure from potential threats and ensure seamless communication between devices.
We encourage you to download and explore the free tools mentioned in this article to enhance your IoT security. Share your experiences and insights in the comments below, and don't forget to explore other articles on our site for more valuable information.
Table of Contents
- Understanding IoT Security and Its Importance
- Setting Up a Virtual Private Cloud (VPC) for IoT Devices
- Using Raspberry Pi for Secure IoT Connections
- Free Download Resources for Secure IoT Connections
- Implementing Secure Communication Protocols
- Best Practices for Securing IoT VPC Connections
- Future Trends in IoT Security
- Conclusion