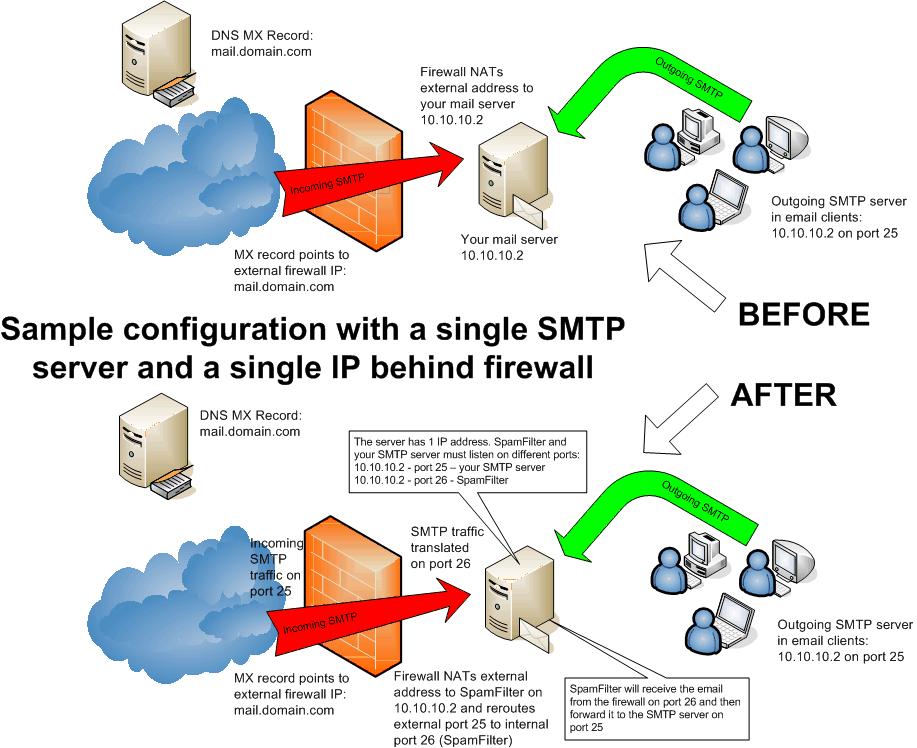
How To Use RemoteIoT Behind Firewall Using Mac Server
In today's interconnected world, managing IoT devices remotely has become a necessity for many businesses. However, one of the most challenging aspects is ensuring secure access to these devices behind a firewall using a Mac server. This article will guide you through the process of setting up and managing RemoteIoT behind a firewall using a Mac server, ensuring both security and efficiency.
As more organizations adopt IoT technology, the need for secure remote access grows. Firewalls act as a critical layer of protection, but they can also complicate the process of accessing IoT devices. By leveraging a Mac server, you can create a secure and efficient system that allows you to manage your IoT devices without compromising network security.
In this comprehensive guide, we will explore the steps required to set up RemoteIoT behind a firewall using a Mac server. Whether you're a network administrator or an IT professional, this article will provide you with the tools and knowledge you need to ensure seamless connectivity and security for your IoT devices.
Read also:Discover The Untold Story Of Adam Scott In Ratatouille
Table of Contents
- Introduction
- Understanding Firewalls and Their Role in IoT Security
- Overview of Mac Server for IoT Management
- Step-by-Step Setup Process
- Implementing Security Measures
- Troubleshooting Common Issues
- Performance Tuning for Optimal Results
- Remote Access Options Using Mac Server
- Best Practices for Managing IoT Devices
- Conclusion and Next Steps
Understanding Firewalls and Their Role in IoT Security
Firewalls are essential components of network security, designed to protect internal networks from unauthorized access. When managing IoT devices, it's crucial to understand how firewalls function and how they can impact remote access.
Types of Firewalls
- Packet Filtering Firewalls: These firewalls inspect data packets and decide whether to allow or block them based on predefined rules.
- Stateful Inspection Firewalls: They monitor active connections and use that information to determine which network packets to allow through the firewall.
- Next-Generation Firewalls (NGFW): These firewalls combine traditional firewall capabilities with additional features like intrusion prevention and application awareness.
Understanding the type of firewall you're working with is essential for configuring remote access securely. For example, a stateful inspection firewall may require specific rules to allow traffic from your Mac server to your IoT devices.
Overview of Mac Server for IoT Management
A Mac server provides a robust platform for managing IoT devices. It offers a range of tools and services that can facilitate secure and efficient remote access.
Key Features of Mac Server
- File Sharing: Allows for centralized storage and sharing of files related to IoT device management.
- Network Services: Supports various network protocols, making it easier to integrate with existing infrastructure.
- Security Features: Includes built-in tools for encryption and user authentication, ensuring secure access to IoT devices.
By leveraging these features, you can create a secure environment for managing IoT devices behind a firewall using a Mac server.
Step-by-Step Setup Process
Setting up RemoteIoT behind a firewall using a Mac server involves several steps. Below is a detailed guide to help you through the process.
Step 1: Configuring the Mac Server
Begin by installing and configuring the Mac server software. Ensure that all necessary services, such as file sharing and network services, are enabled.
Read also:Hdhub4ukids A Comprehensive Guide To Familyfriendly Entertainment
Step 2: Setting Up Firewall Rules
Configure your firewall to allow traffic from the Mac server to your IoT devices. This may involve creating specific rules to permit certain IP addresses or ports.
Step 3: Establishing Secure Connections
Use secure protocols like SSH or TLS to establish connections between the Mac server and your IoT devices. This ensures that data transmitted between the two is encrypted and protected from unauthorized access.
Implementing Security Measures
Security is paramount when managing IoT devices remotely. Below are some measures you can take to enhance the security of your setup.
Regular Updates
Ensure that both your Mac server and IoT devices are regularly updated with the latest security patches. This helps protect against vulnerabilities that could be exploited by attackers.
User Authentication
Implement strong user authentication mechanisms, such as two-factor authentication, to ensure that only authorized users can access your IoT devices.
Troubleshooting Common Issues
Even with careful planning, issues can arise when setting up RemoteIoT behind a firewall. Below are some common problems and their solutions.
Connection Issues
If you're experiencing connection problems, check your firewall rules to ensure that the necessary ports are open. Additionally, verify that your Mac server is configured correctly and that all devices are properly connected to the network.
Performance Tuning for Optimal Results
Optimizing the performance of your Mac server can improve the efficiency of managing IoT devices. Below are some tips for performance tuning.
Network Optimization
Ensure that your network is optimized for handling the traffic generated by your IoT devices. This may involve upgrading hardware or adjusting network settings to improve speed and reliability.
Remote Access Options Using Mac Server
There are several ways to access your IoT devices remotely using a Mac server. Below are some popular options.
SSH Tunneling
SSH tunneling allows you to securely access your IoT devices by creating an encrypted connection between your Mac server and the devices. This method is particularly useful when working behind a firewall.
Best Practices for Managing IoT Devices
To ensure the successful management of IoT devices behind a firewall, follow these best practices.
Regular Monitoring
Monitor your IoT devices regularly to detect any potential issues or security threats. This proactive approach can help prevent problems before they occur.
Documentation
Keep detailed documentation of your setup, including firewall rules, server configurations, and device information. This documentation can be invaluable when troubleshooting or making changes to your system.
Conclusion and Next Steps
In conclusion, managing RemoteIoT behind a firewall using a Mac server requires careful planning and execution. By following the steps outlined in this article, you can create a secure and efficient system for managing your IoT devices.
We encourage you to take action by implementing the strategies discussed in this article. Whether it's configuring your firewall, optimizing your Mac server, or enhancing security measures, each step contributes to a more robust and reliable system. Don't forget to share your thoughts and experiences in the comments section below, and consider exploring other articles on our site for additional insights and tips.
For further reading, consider checking out these trusted sources: